Five critical lessons from the increase in cyber crime
Straightforward steps can minimise the risks that no one can afford to ignore.
The recently-released ACSC Annual Cyber Threat Report, July 2021 to June 2022 provides an overview of key online threats, how the Australian Cyber Security Centre (ACSC) has been responding and crucial advice for individuals and businesses on how they can protect themselves online.
It says since the pandemic began in 2020 cyber threats have grown rampant, particularly from phishing calls and text messages, attacks on video conferencing and insider threats.
In addition, Russia’s invasion of Ukraine this year resulted in destructive malware and sophisticated cyber attacks on European networks.
Australian organisations saw an increase in the number of advanced cyber threats such as extortion, espionage and fraud at large scale. The ACSC received over 76,000 cyber crime reports — a jump of almost 13 per cent on the previous fiscal year.
The ACSC’s top security trends:
- Cyber space has become a battleground.
- Australia’s prosperity is attractive to cyber criminals.
- Ransomware remains the most destructive cyber crime.
- Worldwide, critical infrastructure networks are increasingly targeted.
- The rapid exploitation of critical public vulnerabilities became the norm.
Here are five crucial takeaways from the latest cyber crime data.
- Frequency of cyber crime reports
The number of cyber crime and cyber security incidents is growing and the high number of successful attacks should be a major concern for any business. As cyber crime increases, so does the need for cyber defence and protection.
The ACSC says there is now the equivalent of one report every seven minutes compared to one every eight minutes the previous year.
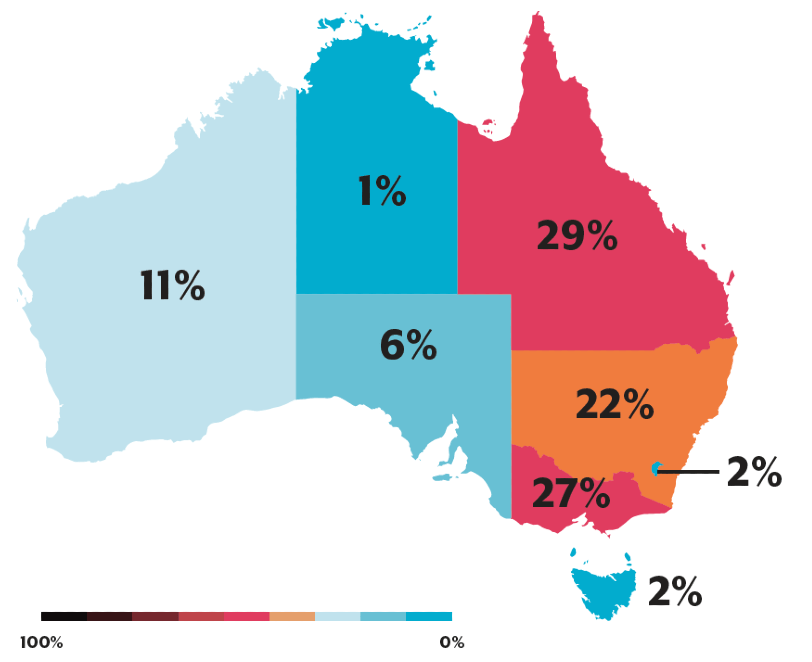
The states hit hardest were Queensland (29 per cent of all cyber crime reports) and Victoria (27 per cent). However, the highest average reported losses from by victims in the Northern Territory (over $40,000) and Western Australia (over $29,000).
- Trending cyber crimes
The three most frequently reported:
- Online fraud: 27 per cent
- Online shopping: 14 per cent
- Online banking: 13 per cent
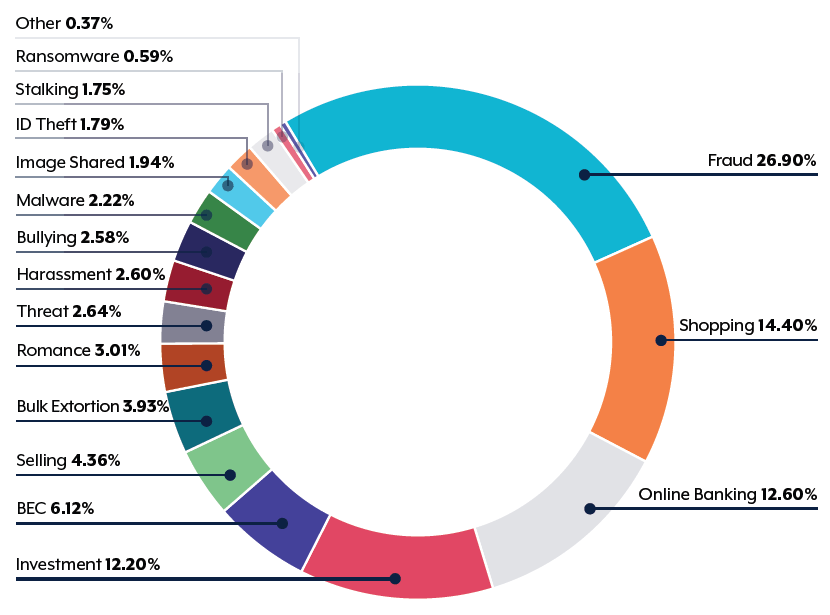
Fraud is most prevalent but the ACSC says ransomware remains the most destructive cyber crime because of its long-lasting impact and impact on data.
Organisations that fall victim to ransomware also face indirect consequences such as reputational damage and leaked information sold on the dark web.
Large enterprises should become aware of this severe threat because top-tier cyber crime syndicates continue to target Australia’s big names.
According to Malwarebytes, LockBit was the ransomware weapon of choice for 2022.
- Top industries targeted
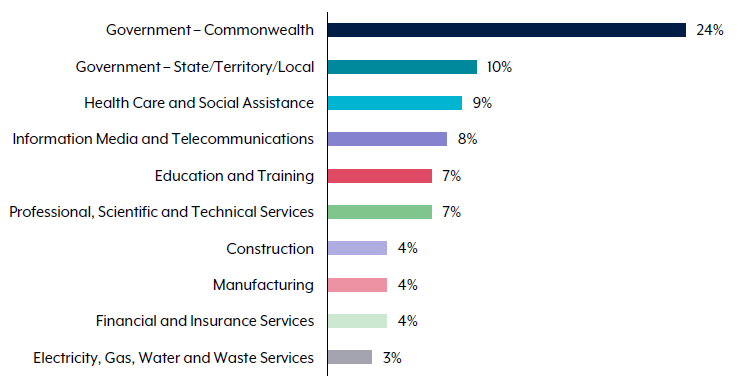
Other than government sectors, the healthcare and social assistance sectors reported the highest number of cyber security incidents at 10 per cent of the total. Information media and telecommunications reported 8 per cent, followed by education and training at 7 per cent.
- Business email compromise
By now, everyone should be aware of the dangers of business email compromise (BEC) attacks. Cyber criminals tend to use BEC on large businesses because they can hijack huge sums without using a malicious payload or URL.
The ACSC’s report shows successful BEC attacks have risen significantly and the average loss per successful BEC increased to over $64,000. Total reported BEC attacks rose to 1,514, with Queensland most vulnerable (389 reports). Western Australia had suffered the most, with several reports of financial losses over $1 million due to BEC, lifting its overall average.
- Cyber defence for organisations and individuals
Cyber Security Minister Clare O’Neil said, “Australia’s unique geostrategic position and information-rich environment mean we all need to work together to build our cyber defences and to ensure all Australians have the tools they need to protect against the impacts of cyber attacks.”
The ACSC recommends following the “essential eight maturity model” as well as other security procedures which involve:
- Restricting administrative privileges
- Patching or updating operating systems
- Implementing multi-factor authentication
- Conducting regular back-ups
- Configuring your email security settings
- Initiating application controls on workstations and servers
- Denying corporate computers direct internet connectivity
Individuals should look to secure devices and accounts. This means:
- Turning on automatic updates for all devices (mobiles, phones, etc) and updating applications, programs, and smart devices.
- Activating multi-factor authentication across all your accounts including email, banking, and social media.
- Backing up your devices regularly (every three to six months).
- Creating strong unique passwords for every account.
First line of defence
To reduce the risk of payment error and fraud, accounts payable (AP) managers should conduct call-back controls to ensure they pay invoices to the correct payee.
Here are some of the common challenges associated with AP teams conducting call-backs:
- They don’t independently source supplier contact details.
- They rely on return messages and incoming information.
- They don’t ask the correct questions.
- The people conducting them aren’t trained to detect fraud.
Call-back controls are essential every time you onboard a new supplier or update an existing supplier. Call-back verification is a simple, effective solution and your first line of defence.
The bottom line
Statistics show sophisticated cyber crime is a severe problem and there are no signs of it slowing down in 2022.
Anyone can fall victim to cyber crime, but being aware and understanding how these threats are created, you can minimise the risk.
Gerard Mondaca is community security manager at Eftsure.
Graphs sourced from the Australian Cyber Security Centre Annual Cyber Threat Report.






